In 2020, we saw a distinct shift in the cyber threat landscape, with ransomware becoming the most significant cyber security threat faced by organisations. The COVID-19 pandemic also forced organisations to rapidly change how they operate – creating new opportunities for threat actors in the process. Remote working meant threats around offsite access and infrastructure came to the forefront, offering new challenges to securing organisations.
Every year we summarise what we’ve seen over the previous 12 months in our Cyber Threats Retrospective report. It highlights the most prolific cyber threat trends, exploring their wider impact on organisations, business and society.
Below we outline five threat trends we believe are continuing to be prominent in 2021, along with how you should respond.
1. Ransomware
While ransomware was a major threat in 2019, threat actors went public in 2020. Many now exfiltrate data from their victims before encrypting their files and announcing they’ve compromised them on public leak sites.
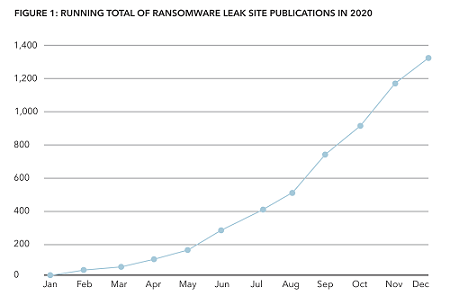
They then set a deadline by which the ransom must be paid, and if victims refuse, publish stolen data on these sites, adding data protection and regulatory issues to the challenge of restoring operations after an attack.
The use of leak sites has put serious pressure on victims to pay ransom demands and provided clear insight into the operational tempo of many ransomware threat actors. The scale and intensity of incidents in 2020 was striking, with ransomware dominating the cyber threat landscape across all industry sectors and locations.
The number of ransomware actors also increased sharply last year. The perceived profitability of human-operated ransomware attacks has attracted new players, and established criminals have added ransomware to their portfolios.
Human-operated ransomware is likely to continue to grow as a threat this year. Organisations that haven’t already taken steps to understand and reduce their vulnerability to these attacks should act now. We published a white paper last year detailing how organisations can reduce the risk of a ransomware attack.
2. Using current affairs as bait
Phishing is not a new tactic – both criminal and espionage threat actors regularly make use of current affairs to lure recipients into clicking on a malicious link or downloading malicious content. During 2020, news concerning the COVID-19 pandemic was no exception, with many threat actors quickly adapting their material to incorporate pandemic-related themes in their campaigns.
These lures matched the ‘stages’ of the pandemic seen in the news. Initially they featured advice around staying safe, and the availability of products such as face masks and testing kits, moving on to news of vaccines and remote working. As financial aid schemes were rolled out, we observed spoofed websites designed to harvest credentials or personal information. Threat actors are still capitalising on the pandemic in 2021 with reports of cyber criminals using phishing emails and text messages requesting payment details to receive a vaccine.
Healthy scepticism is your friend when combating phishing. Organisations should remind their employees of what to look for in a phishing email or site, such as suspicious links or attachments, unfamiliar source addresses and unexpected requests which fall outside of normal business practices. Regular test exercises will also help to keep staff alert.
3. Supply chain attacks
Supply chain compromise remained a prominent attack vector in 2020 with several high-profile incidents. In some cases, multiple threat actors compromised the same ‘supplier’ entity independently, complicating the scoping, response, and attribution of incidents.
The most high-profile incident, Solorigate, provided a sharp reminder of the vulnerability of supply chains. The SolarWinds ‘Orion’ IT monitoring product was backdoored with previously undocumented malware known as SUNBURST. This was distributed to up to 18,000 customers via SolarWinds’ legitimate update mechanism and used to surgically target a small number of organisations of specific interest to the actor.
The threat actor that developed SUNBURST displayed a high level of sophistication and remained under the radar for months. In its wake, organisations should be asking themselves about access privileges and whether they are giving IT management and security software too much leeway.
They should also be assessing whether their threat detection capabilities can identify malicious activity across their environment and whether any changes could be made to identity and access management systems to detect the abuse of trusted or privileged access.
4. Social engineering
In 2020, threat actors continued to perfect their social engineering techniques and became more bold in engaging with targets. Social media platforms are used not only for reconnaissance but increasingly to directly interact with targets over multiple mediums.
Our analysis showed various threat actors using LinkedIn to find and engage with targets. They created fake recruiter profiles, building trust with their victims, sometimes over a period of weeks or months of interaction. Once this was established, the conversation reportedly moved to other means of communication including WhatsApp, email, and even phone calls. Victims were tricked into opening malicious attachments disguised as job specifications.
Human error is still a huge vulnerability to any cyber security defence, and we expect to see individuals continue to be targeted as a path to gaining access. Organisations should seek to build a secure culture and ensure their entire workforce – no matter their role – adopt the secure behaviours and attitudes needed to keep the organisation safe.
5. Rise of the defenders
Though the trends listed above may seem daunting, there was some good news last year. Public sector entities, legislative branches and private sector organisations have been sharpening their cyber strategies and coordinating efforts to tackle malicious cyber activity. Sanctions and indictments have formed an increasingly prominent part of deterring and disrupting malicious cyber activity. 2020 also saw the European Council impose its first round of restrictive sanctions (including a travel ban and asset freezing) against multiple individuals and entities in response to global cyber incidents.
Private sector companies are also taking steps to cut off key infrastructure from operators, disrupting their ability to perform new infections or communicate with existing compromised hosts. While threat actors will ultimately continue to conduct their operations, it is clear the takedown of key threat actor infrastructure can cause significant disruption to their operations.
Both the public and private sectors have grown increasingly bold in attribution and in the willingness to share information. At a minimum, public attribution serves as a warning this activity has not gone unnoticed and generates a greater awareness of the cyber threat landscape, and a greater opportunity for defence efforts.
About the author
Krystle Reid is a threat intelligence manager at PwC UK.
Related resources
More support on business
Read our articles, eBooks, reports and guides on risk management.
Risk management hubeBooks on risk