Most Excel users know about the dangers of running macros received from an untrusted source. However, as Microsoft strengthens its security procedures relating to macros, the danger might increasingly come from another direction: Excel add-ins and, in particular, .XLL files. Think before you click!
Moving on from macros
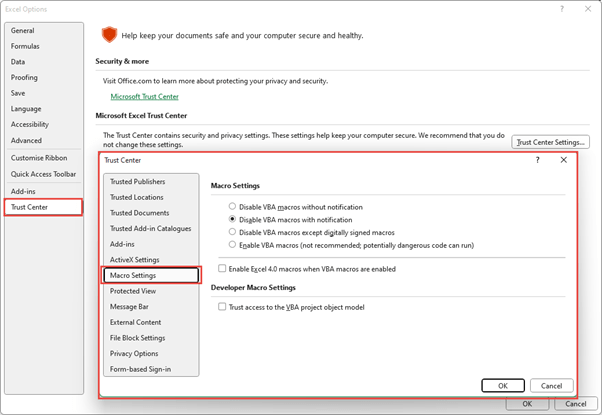
For many years we have been accustomed to the dangers of macros in Microsoft Office documents. Because macros are written in a programming language, Visual Basic for Applications, there is plenty of scope for them to be used maliciously. Accordingly, Microsoft has introduced a series of safeguards to reduce the risk. Since the introduction of Office 2007, macros cannot be saved in a standard .XLSX Excel file but instead workbooks containing macros have to be saved with the .XLSM extension. The Excel Trust Centre within File, Options has a specific Macro Settings section that allows restrictions to be imposed on running macros:
In addition, since the middle of last year, Excel has blocked macros by default when the file source is untrusted:
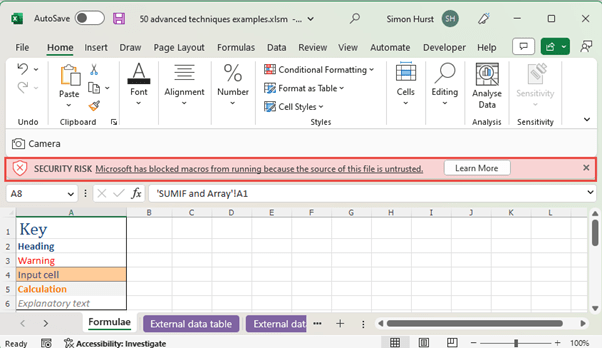
Note however that this additional protection applies for recent Office updates only. Older versions, or installations that have not been updated, may not have the benefit of this security improvement.
Excel Add-ins
So, as Microsoft cuts down the opportunities to exploit macro vulnerabilities, attention turns to other possible attack vectors. In its recent threat report, released on 13th January, the National Cyber Security Centre listed “Increased use of XLL add-ins as an infection vector”. Citing Cisco Talos research, the threat report highlights Microsoft’s action on macros as the likely cause for the change in approach.
Excel add-ins are often used to add functionality to Excel and can be distributed as .XLL files. Just like macros, add-ins have the ability to carry out malicious actions, such as installing malware, as well as adding legitimate functionality. Although Excel has options to ensure the user is prompted before running add-ins, as is the case with macros, leaving individual users with the decision as to whether or not to run an add-in is far from a secure approach to security.
The Cisco Talos report includes plenty of technical details on the threats posed by .XLL files together with examples of specific recent malware that uses these files and a timeline of the increased prevalence of .XLL-based attacks.
Adding to the details in the Cisco Talos report, Palo Alto’s Unit 42 also details the mechanics of how a malicious .XLL file can infect a system and includes a case study around the information stealing, remote access trojan (RAT) Agent Tesla malware.
The NCSC has issued guidance for organisations on how to defend against these types of attacks which can often come in the form of phishing attacks.
Be careful out there.
Archive and Knowledge Base
This archive of Excel Community content from the ION platform will allow you to read the content of the articles but the functionality on the pages is limited. The ION search box, tags and navigation buttons on the archived pages will not work. Pages will load more slowly than a live website. You may be able to follow links to other articles but if this does not work, please return to the archive search. You can also search our Knowledge Base for access to all articles, new and archived, organised by topic.

